API Security
At Network International, we take the security of our APIs very seriously. We understand that our clients trust us with their valuable data, and we are committed to protecting it at all times. In this section, we explain the security measures we have in place to ensure the confidentiality, integrity, and availability of our API services. The following measures are implemented to ensure secure communication between your application and our APIs:
SSL/TLS Encryption
All communication between our API clients and servers is encrypted using SSL/TLS protocols. This ensures that data in transit is protected from unauthorized access, interception, and tampering. We use strong encryption algorithms and certificates to secure the communication channels and ensure the authenticity of the endpoints.
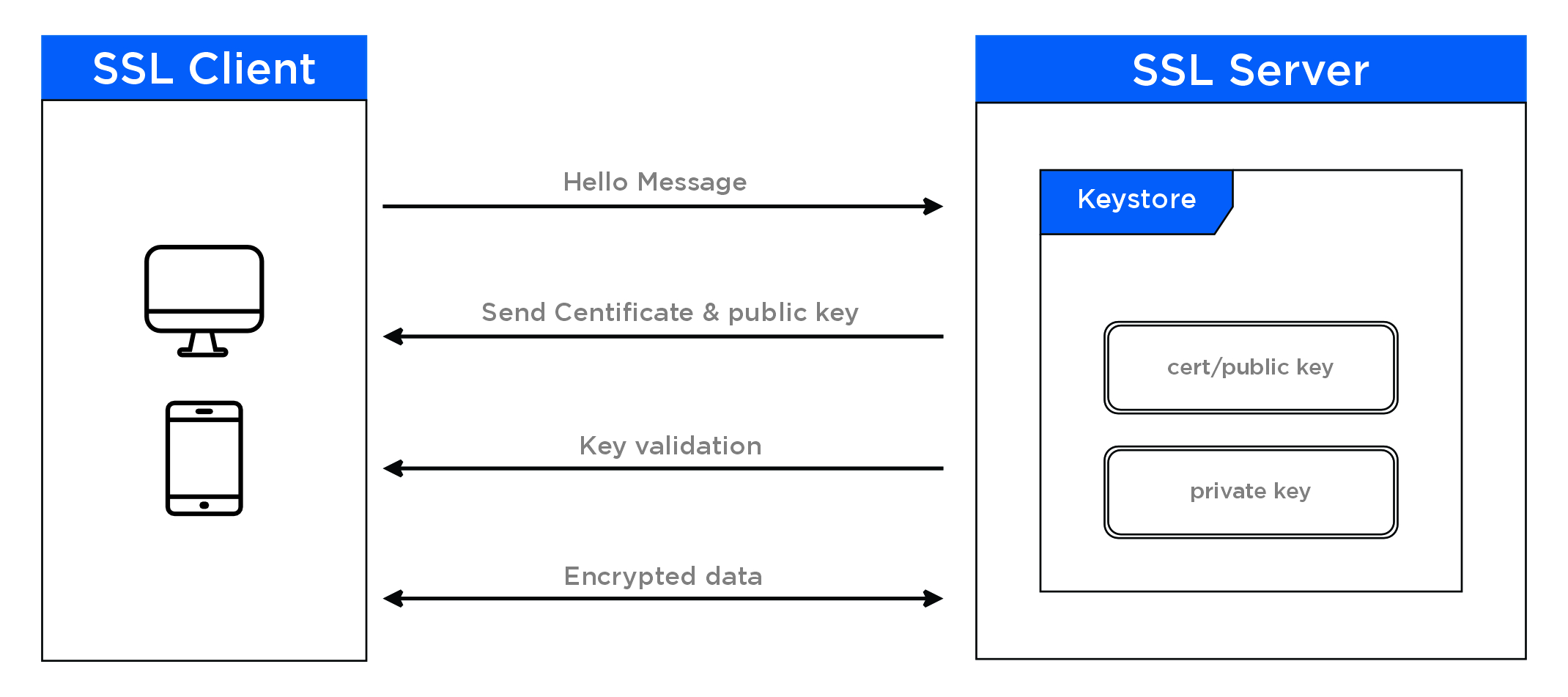
One-Way SSL
To enhance the security of our API services, we use one-way SSL authentication. This means that the server sends its digital certificate to the client, which contains the server's public key. The client can then use this public key to encrypt data and send it securely to the server. The server can then decrypt the data using its private key. One-way SSL authentication verifies the identity of the server and ensures that only trusted clients can access our API services, while preventing unauthorized parties from intercepting or manipulating communication channels.
SSL Implementation
API communication happens over a secure TLS channel for enforcing encryption of API payload. Server Setup: The server generates a digital certificate containing its public key and installs it on its server software.Client Connection: The client initiates a connection to the server using SSL/TLS.Server Certificate: The server sends its digital certificate to the client during the SSL/TLS handshake process.Client Verification: The client verifies the server's certificate by checking its expiration date, issuer, and other relevant details to ensure that it was issued by a trusted authority and has not been tampered with.Pre-Master Secret: The client generates a random pre-master secret and encrypts it using the server's public key from the server's digital certificate.Master Secret: The server decrypts the pre-master secret using its private key to obtain the shared secret. Both the client and the server use the pre-master secret to generate the master secret, which is used to encrypt and decrypt data during the session.Encryption: The client and server use the master secret to derive session keys, which are used to encrypt and decrypt data exchanged during the SSL/TLS session.
OAuth Authentication
We use OAuth authentication to authorize access to our API resources. This allows our clients to obtain access tokens with specific scopes that grant them access to only the resources they need. This ensures that clients can access the data they require, while ensuring that no unauthorized access occurs. We use industry-standard OAuth frameworks and best practices to secure the authentication and authorization processes.
OAuth Flow Description
- The client application sends an authorization request to the API gateway.
- The API gateway receives the authorization request and responds with an access token to the client.
- The client application includes the access token received from the API gateway in the standard authorization header of each API request.
- The API gateway verifies the access token for each API request it processes.
- The access token is placed in the standard authorization header of the client requests, typically in the format "Bearer XXXXXX_ACCESS_TOKEN_XXXXX".
- The client application must retrieve a new access token before the expiration of the existing token to ensure continued access to protected resources.
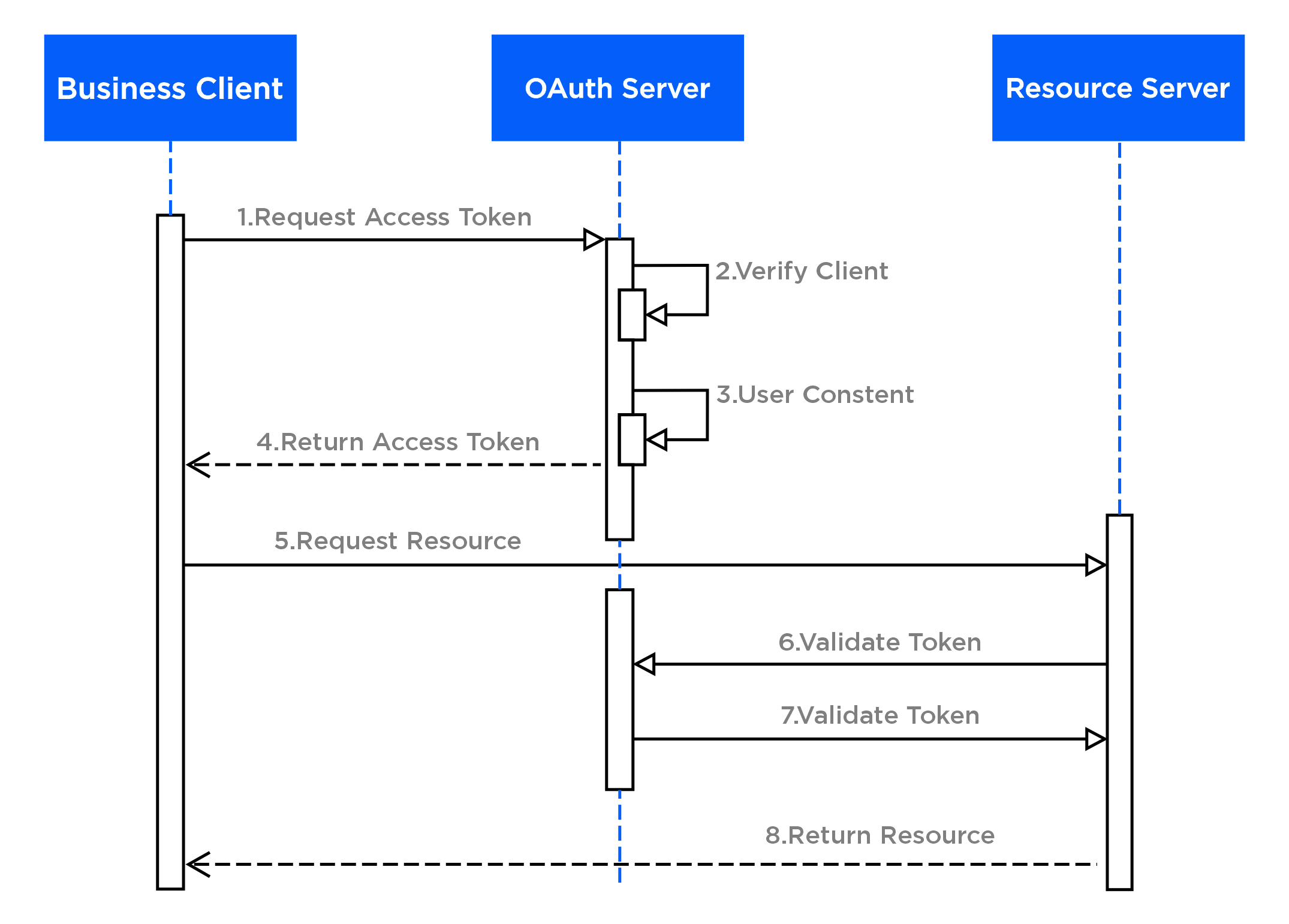
This flow ensures that the client application is authorized to access protected resources on behalf of the user, without requiring the user's credentials to be shared with the client application. By including the access token in the authorization header of each API request, the API gateway is able to verify the token for each request, ensuring that only authorized requests are processed. Finally, the requirement to retrieve a new access token before the expiration of the existing token ensures that access to protected resources is maintained and secure.
 Overview
Overview API Security
API Security Onboarding Journey
Onboarding Journey Appendix
Appendix